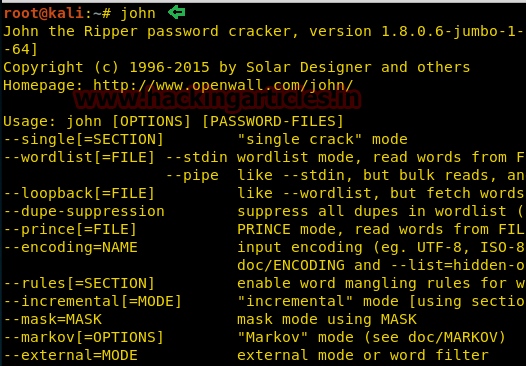
“John the Ripper” – is a fast password cracker. Its primary purpose is to detect weak Unix passwords.
- Cracking Linux Passwords With John The Ripper
- Crack Htpasswd John The Ripper Linux Download
- Crack Password Hash John The Ripper
- Crack Htpasswd John The Ripper Linux Server
Most likely you do not need to install “John the Ripper” system-wide.
Cracking an Ubuntu password with John the Ripper is very easy. All that is needed is a good wordlist and the John The Ripper utility. Install the John the Ripper password cracking utility.
Instead, after you extract the distribution archive and possibly compile the source code (see below), you may simply enter the “run” directory and invoke John from there.
John the Ripper. John the Ripper is a great tool for cracking passwords using some famous brute for attacks like dictionary attack or custom wordlist attack etc. It is even used to crack the hashes or passwords for the zipped or compressed files and even locked files as well. It has many available options to crack hashes or passwords. To use John the Ripper. Step 1: Combine the passwd & shadow file to one file named crack. Command: cat /etc/passwd Desktop/crack && cat /etc/shadow Desktop/crack Combining Passwd & Shadow. Then try reading the files individually with any text editor you like(leafpad, nano, vim, or simply cat it). The $JOHN/john.pot file is also used to not load password hashes that you already cracked when you run John the next time. To retrieve the cracked passwords, run: john -show passwd While cracking, you can press any key for status, or 'q' or Ctrl-C to abort the session saving its state to a file ($JOHN/john.rec by default).
Compiling “John the Ripper”
Step 1: Download the latest version of ““John the Ripper”” and its signature
Step 2: Confirm the signature
This is a safety measure as we are dealing with dangerous thing.
Install the public key:
Check the signature:
You will see the message similar to the above. Ignore the warning as long as it says Good signature from “Openwall Project … “.
The warning is normal, see http://www.kernel.org/signature.html for more details.
Step 3: Uncompress and compile the sources
Note the make target for your system and type:
Where <system> is the appropriate make target. Alternatively, if your system is not listed, use:
If everything goes well, this will create the executables for John and its related utilities under “../run/”.
Alternatively, you may copy the entire “run” directory to anywhere you like and use John from there.
Now you can change directory to there and test John, like this:
Installing “John the Ripper” on Ubuntu
Execute the next command to install “John the Ripper” on Ubuntu:
Installing “John the Ripper” on CentOS/RHEL
Execute the next command to install “John the Ripper” on CentOS/RHEL:
John is different from tools like HDRA. Hydra makes a blind brute force attack by trying the user name / password combination on the FTP server or telnet server’s service backend. However, John needs hashing first. So, the bigger challenge for hackers is to get the hash that needs to be cracked first. Today, it’s easier to crack hashes with the free rainbow table available online. Just go to one of the sites and submit the hash; if the hash consists of a common word, the site will display that word almost immediately. Rainbow table basically stores common words and corresponding hashes in a huge database. The larger the database, the more words it contains.
But if you want to crack passwords locally on your system, John is one of the great tools worth trying. John is one of the top 10 security tools in Kali Linux. On Ubuntu, it can be installed through the Synaptic Package Manager.
In this article, I will show you how to use the unshadow command together with John to crack a user’s password on a Linux system. On Linux, the user name / key details are stored in the following two files.
Cracking Linux Passwords With John The Ripper
The code is as follows:

/etc/shadow
The actual password hash is stored in / etc / shadow; you can access the file as long as you have root access to the machine. So try to access the file from your own Linux system. Or create a new user with a simple password first. I’ll create a new user on my Linux system called happy with the password chess.
The code is as follows:
Adding user `happy’ …
Adding new group `happy’ (1001) …
Adding new user `happy’ (1000) with group `happy’ …
Creating home directory `/home/happy’ …
Copying files from `/etc/skel’ …
Enter new UNIX password:
Retype new UNIX password:
passwd: password updated successfully
Changing the user information for happy
Enter the new value, or press ENTER for the default
Full Name []:
Room Number []:
Work Phone []:
Home Phone []:
Other []:
Is the information correct? [Y/n] y
[email protected]:~#
For the sake of demonstration, it’s better to use a simple password, so you don’t have to wait too long. Since our new user has been created, we can now crack their password.
The unshadow command will basically combine the data of / etc / passwd and / etc / shadow to create a file with user name and password details. The usage is quite simple.
The code is as follows:
Crack Htpasswd John The Ripper Linux Download
Usage: unshadow PASSWORD-FILE SHADOW-FILE
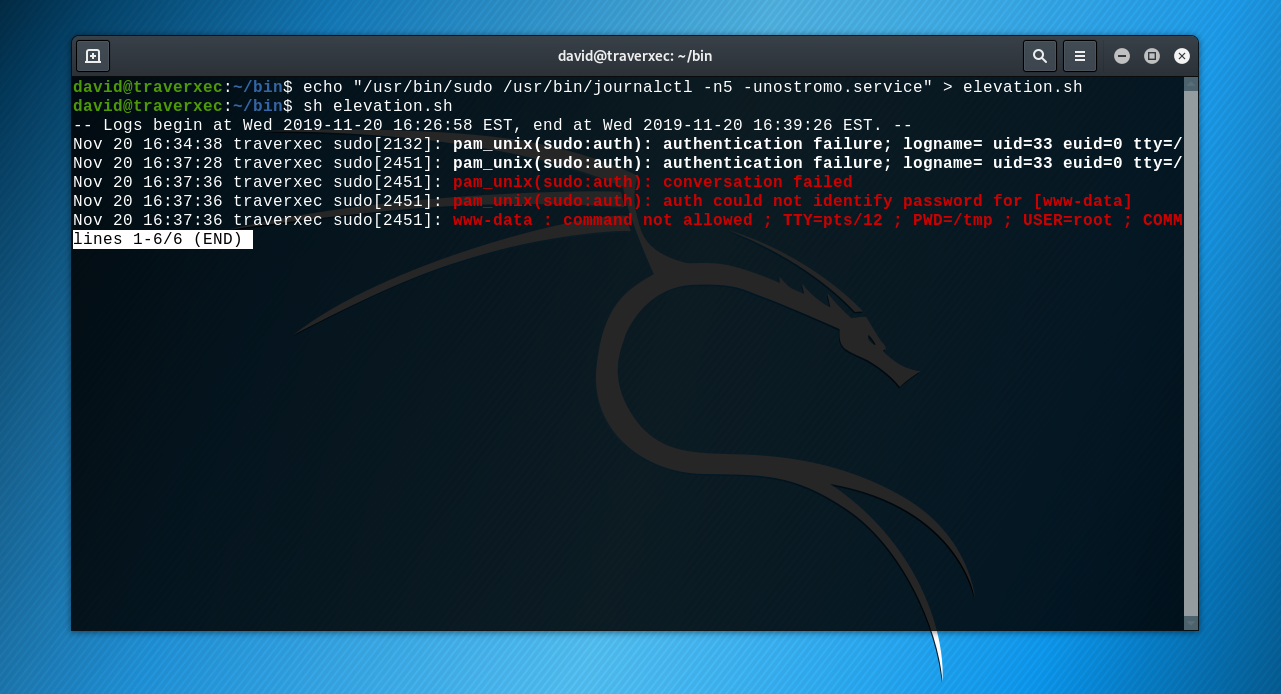
[email protected]:~# unshadow /etc/passwd /etc/shadow > ~/file_to_crack
We redirect the output of the unshadow command to a file named file_ To_ New file for crack.
step
Now let’s take a look at the specific steps. After cracking the password successfully, the jhon.pot Password only:
1. Enter the / root / john-1.7.8/run directory and read / etc / shadow with the tool unshadow provided by Jhon
The code is as follows:
Eg: for root users, you can cat / etc / shadow > / root / john-1.7.8/run/ passwd.txt
The first step is to use single crack mode to crack
The code is as follows:
Specifically for people who use accounts as passwords, they will try a variant of the user name john.conf Medium[ List.Rules Rules defined in: single]
The code is as follows:
If the crack is successful, you can view it jhon.pot Or use:
The code is as follows:
3. The second step is to use wordlist mode to crack
Wordlist mode is a relatively simple mode, as long as you determine where the dictionary file is jhon.conf There is a default dictionary file ‘wordlist = $John’ in the configuration file/ password.lst ’In the run directory password.lst File, wordlist Mode rule in jhon.conf Medium[ List.Rules : wordlist] module definition in[ List.Rules There’s another one under wordlist[ List.Rules The: NT] module is a variant rule that defines rules.
The code is as follows:
Or
The code is as follows:
The fourth step is to use incremental mode to crack
Incremental is the most powerful mode. It will enumerate all combinations and crack them as passwords. It is very time-consuming. There are [in] in the configuration file cremental:All ],[In cremental:Alpha ],[In cremental:Digits ],[In cremental:Alnum ],[In cremental:LanMan ]And so on. Each module name has a corresponding date file under run.
The code is as follows:
Crack Password Hash John The Ripper
Crack Htpasswd John The Ripper Linux Server
5. The fifth step is to use external mode to crack
External allows users to write their own cracking mode of C language jhon.conf We already have some crack mode programs.
Parameter interpretation
–Stdout outputs the results to the screen
–Restore continues to execute from the place where the last decryption was interrupted. If the execution is interrupted by Ctrl + C, the current status will be stored in a document named restore. Use — restore to read the location of the last interrupt from restore, and then continue to crack
–Session sets the name of the current log file
–Make charset character frequency table, which can be used in incremental mode
–Show shows that the password has been cracked because john.POT No account information is stored. When using show, you should input the relevant passwd file
–Test to test the cracking speed of various types of passwords executed by the machine
–Users can only crack the password of an account, which can be the user name or uid number. Adding ‘-‘ before it means not cracking the password of the relevant user
–Groups only crack the password of users in a group. Adding ‘-‘ before it means not cracking the password of users in a group
–For users who use a certain type of shell, the prefix ‘-‘ means no cracking
–Salt can only crack the password whose salt is greater than count. Salt is the basic unit used by UNIX as password coding
–Predefined password cracking types DES / bsdi / MD5 / BF / AFS / LM/